Zello has become a leading push‑to‑talk (PTT) application, letting users convert their smartphones or radio devices into walkie‑talkies over IP. While its built‑in features serve many needs, a curious tech community asks: How to make Zello mods what app to use ?
In this guide, you’ll learn:
-
What “modding” Zello means, and why people pursue it
-
The technical tools & apps often used for customization
-
Step‑by‑step methods (with caution)
-
Risks, legal concerns, and how to mitigate them
-
Safer and officially supported paths using Zello’s SDK / APIs
-
Troubleshooting, best practices, and use cases
Before you proceed: modifying or redistributing a modded version may violate Zello’s terms of service, and could expose you to security or legal risk. Always use a test device not tied to your primary account, and consider using the official SDK or API route instead of heavy customization on the client side.
1. Why People Want Zello Mods

People mod Zello for several reasons:
-
Customization — change sounds, UI themes, notification behavior
-
Extended features — add hidden or premium behaviors
-
Radio / hardware adaptation — integrate Zello more tightly with radio devices that may lack touchscreens or standard Android UI
-
Automation / scripting — embed auto‑actions, macros, or event triggers
-
Novel experiments / learning — for tinkerers who want to explore how apps work under the hood
While modding offers flexibility, the tradeoff is stability, security, and compliance.
2. What Is Zello & How It Works
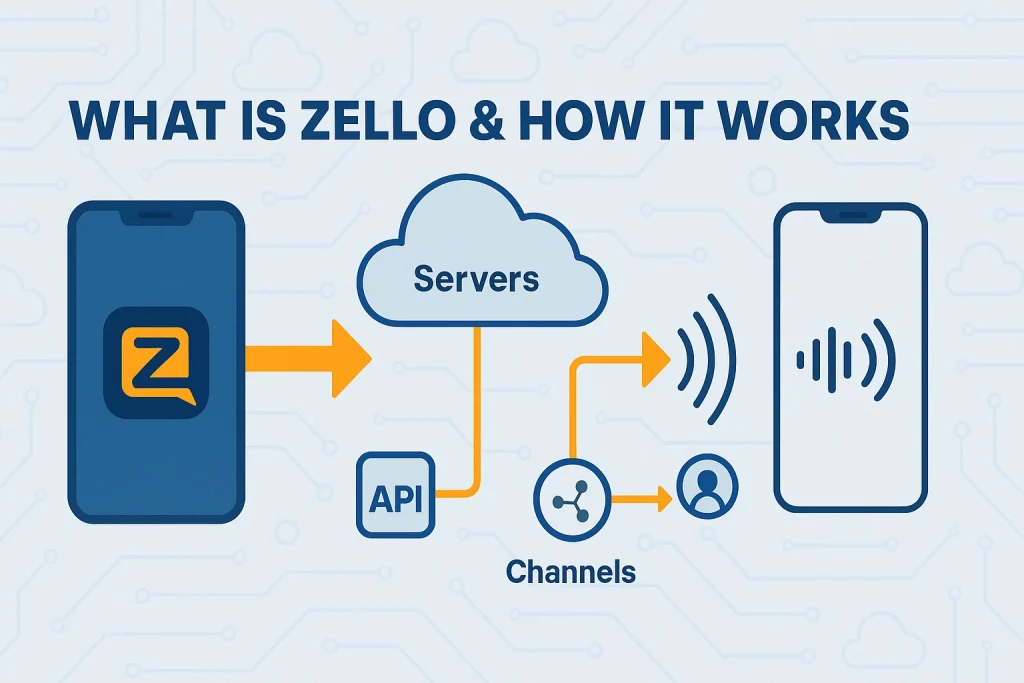
To understand how mods work (or don’t), you need a baseline understanding of Zello’s architecture.
What Zello is:
-
Zello is a live voice push‑to‑talk communication platform, turning devices into walkie‑talkies over IP.
-
It supports real‑time voice messages, group / channel communications, dispatch calls, alerts, message playback, and location features.
-
Zello offers an SDK and API to embed push‑to‑talk functionality into your own app.
How Zello communicates:
-
The client connects to Zello’s servers (or internal infrastructure) using a WebSocket / custom TCP protocol.
-
Voice data is streamed in real time, with buffering for latency.
-
Channels / group logic, messaging, history, user profiles, status, alerts, etc. are managed through the Zello backend.
-
Some client logic (e.g. UI, sound processing) is handled locally on device side.
Because much of the core logic resides server-side or in binary client libraries, modding client behavior can only go so far (versus completely rewriting or integrating via SDK).
3. Risks, Legality & Ethical Considerations

Before diving into modding, you should be aware of the potential downsides. This section should ideally be placed prominently in your published version (as a caution/disclaimer).
3.1 Terms & License Violations
-
Many apps’ Terms of Service explicitly forbid reverse engineering, modifying, or redistributing modified versions.
-
Using or distributing a modified client may lead to account suspension or bans.
-
In some jurisdictions, reverse engineering software is legally restricted (though often allowed for interoperability, depending on local law).
3.2 Security, Integrity & Malware Exposure
-
Tampered APKs may embed malware, backdoors, or unwanted tracking.
-
Signature mismatches or certificate issues can lead to app crashes or detection.
-
Modded clients might inadvertently expose credentials, logs, or internal endpoints.
3.3 Update / Compatibility Risks
-
Every time Zello updates their official app, mods may break or be flagged.
-
Custom modifications might conflict with future patches, leading to data loss or app instability.
3.4 Ethical Considerations
-
If you distribute mods widely, you may undermine licensing, revenue models, or user security.
-
Some mod features may inadvertently enable misuse (e.g. impersonation, unauthorized access to channels).
Mitigation best practices:
-
Always back up the original client and your data
-
Use test / disposable devices for experimentation
-
Limit mod distribution; don’t share publicly without legal clarity
-
Document your changes, maintain version controls
-
Consider fallback to official SDK / API paths for production or wider deployment
4. Tools & Apps Commonly Used in Modding
To mod an Android (or Android‑based radio) version of Zello, these tools and apps are often employed. (In some cases, iOS modding is significantly more restrictive and often not feasible without jailbreaking, which we won’t cover here.)
4.1 Root vs No‑Root Options
-
Rooted devices provide full file system access, the ability to write to
/system, override protected directories, inject system libs. -
No-root methods rely on user-space hacks—overlays, hooking frameworks (e.g. Xposed, Magisk modules), data directory changes, permissions, or repackaging of APKs.
-
Rooted strategies give more power but also more risk: bricking devices, voiding warranties, or being detected by integrity checks.
4.2 Android Debug Bridge (ADB)
ADB is a command-line tool to interact with Android devices over USB or network:
-
adb devices— list connected devices -
adb shell— open a shell on device -
adb pull/adb push— copy files to/from device -
adb install/adb uninstall— install or remove APKs -
adb logcat— view logs in real time (for debugging)
These commands are staples in modding workflows.
4.3 APK Decompilers / Editors
To inspect or change app internals:
-
APKTool — decompile, rebuild, decode resources
-
jadx / JD‑GUI / Dex2Jar — decompile classes.dex into Java/Smali code
-
Resource editors / ZIP tools — edit
res/,assets/, XML files -
Smali / Baksmali — modify low-level bytecode representation
These allow examining the app’s internals and making modifications.
4.4 Signing Tools
After modifications, you need to re-sign the APK:
-
apksigner (Android SDK tool)
-
jarsigner
-
Custom private key or working around signature mismatch code (if present)
4.5 Overlays, Hooking Frameworks & Modules
Especially on rooted devices, modules can dynamically patch behavior at runtime:
-
Xposed Framework / EdXposed / Riru / LSPosed: modules can intercept methods, modify behavior
-
Magisk modules — systemless tweaks
-
Frida / Substrate / hooking libs — dynamic instrumentation
These tools allow changes without fully rebuilding the APK (for some behavior hooks).
4.6 Launchers / Overlays for Radio Devices
Some radio devices lock down UI to show only Zello. You may need:
-
Custom launchers / alternate launch interfaces
-
Overlays to intercept keypress or hardware buttons
-
scrcpy (or screen mirroring) to proxy UI control to PC for configuring features
5. Step‑by‑Step: How to Make Zello Mods
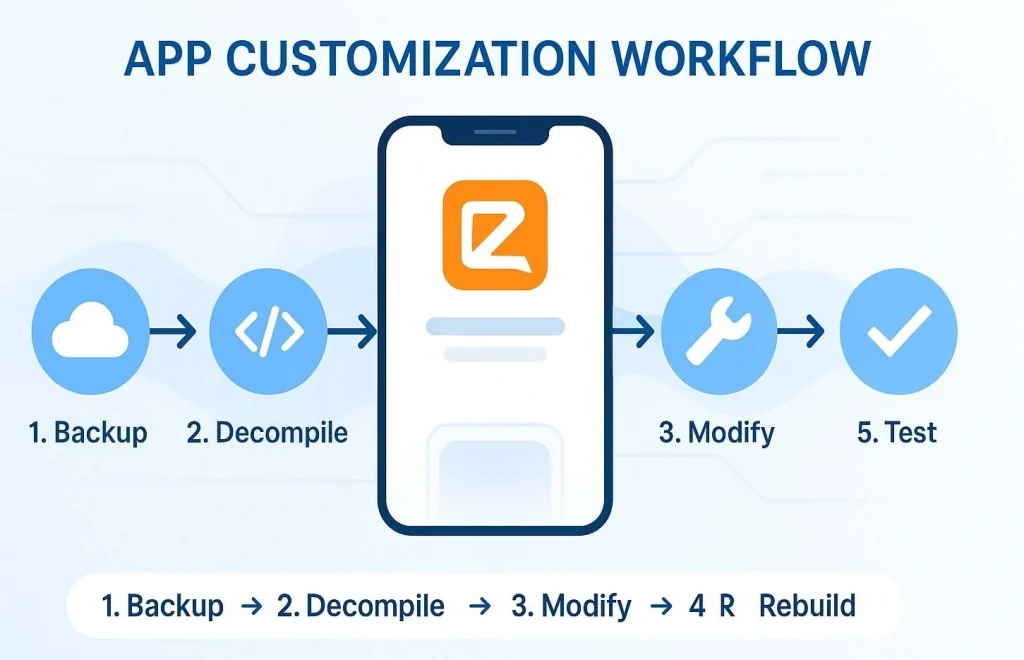
Below is a generalised workflow. Your specific device, Android version, or Zello version may require adaptations.
5.1 Backup Original APK & Data
- On device with debugging, find the Zello package path. Common path:
/data/app/com.zello…/base.apk adb pull /data/app/com.zello…/base.apk ./original_zello.apk- Also back up app’s data (if possible):
adb backup -f zello_data.ab com.zello.… - Keep records of version, build, and signatures.
5.2 Decompile & Explore
- Use
apktool d original_zello.apk— results a folder withres/,AndroidManifest.xml,smali/etc. - Look in
res/raw,res/raw,assets/— for audio, sound, configuration files - Inspect
smali/or decompiled Java to see method calls, resources, UI entry points
5.3 Modify / Inject Custom Features
-
Replace or change sound files (e.g.
.wav,.mp3) in the resource directories -
Modify XML layout / menus to add toggles, new UI buttons
-
In smali / bytecode, patch methods (e.g. skip signature checks, change behavior)
-
Add new classes or smali files for extra logic (advanced)
5.4 Rebuild & Sign
apktool bto rebuild into a “dist” directory- Use
apksignerorjarsignerwith your key: apksigner sign --key mykey.pk8 --cert mycert.x509.pem modded.apk- If Zello has built-in integrity checks, you may need to patch them out (via smali)
5.5 Install & Test
-
adb install -r modded.apk(or uninstall old then install) -
Run logcat:
adb logcat | grep com.zelloto monitor errors -
Test all features (PTT, audio, channels, history, reconnects)
-
If crash or error, inspect stack traces, missing resources, signature mismatch
6. Special Modding for Zello Radio / Hardware Devices

For devices like android‑based radios (e.g. “Zello radios”) where UI is locked or limited, certain additional steps are needed.
6.1 Using scrcpy or Mirroring
-
Use scrcpy (or similar) to mirror device screen on PC and control it.
-
This helps in navigating configuration screens that may not be accessible via hardware buttons.
-
On limited devices, this becomes your method to test UI adjustments.
6.2 Launcher Overrides & Firmware Hacks
-
Some radios prevent launching anything but Zello. To mod, you may need to:
-
Replace the system launcher
-
Modify firmware (e.g. in
/system/appor/system/priv-app) -
Enable hidden “developer mode” launchers
-
Inject an alternate UI entry point
-
Warning: Firmware hacks risk bricking the device or voiding warranty.
6.3 Pushing Custom Sounds / Files
-
Use
adb push custom_sounds /sdcard/Zello/(or appropriate path) -
Use shell to verify path:
adb shell ls /sdcard/Zello/ -
Some devices mount as read-only; remount or push into internal storage if permissions allow
7. Safer & Official Alternative: SDK / API Integration
Because modding the client has many risks, the recommended path in many use cases is to use Zello’s SDK or APIs.
7.1 Zello Mobile SDK
Zello recently released a new Mobile SDK which allows embedding Zello’s core PTT features into your own app, avoiding the need to tamper with the client.
Key features:
-
Voice, image, text messaging with channels
-
Message history, replay
-
Profile and availability management
-
Location, alerts, dispatch features
-
Works on Android, iOS, React Native
-
Available as a “blank installation package” (for custom integration) or “example app” with full features ready to test.
Installation on Android:
-
Add Zello Maven repository in Gradle
-
Add dependencies:
com.zello:sdk,com.zello:core,com.zello:zello(and Firebase for push) -
Follow their docs to integrate login, PTT button, channel logic, messaging
Using the SDK gives better long-term stability, compliance, and simpler maintenance.
7.2 Zello Channel API (WebSocket-based)
Zello offers a Channel API (in beta) using WebSockets to build your own lightweight client logic.
-
Open source SDKs exist for iOS, Android, Web clients.
-
You can embed only the client logic you need, customizing UI and behavior.
7.3 Zello Bridge & Gateway Integrations
For hardware / radio bridging, Zello Bridge can connect Zello to radio systems / gateways.
-
Safer for production use
-
Uses official integration rather than client modding
8. Best Practices & Safety Tips
-
Always retain the original, unmodified APK and data backups
-
Work on spare/test devices, not critical or personal devices
-
Use robust version control / change logs when modifying
-
Keep changes as minimal as possible (less patching, minimal smali hacks)
-
Monitor for security behavior — validate network traffic, check for unintended endpoints
-
If distributing mods, include disclaimers and limit to closed groups
-
Always stay updated with official Zello changes (API, SDK, client updates)
-
If you rely on mods for production or external use, plan migration to SDK/API path
9. FAQs & Troubleshooting
Q: The modded app crashes on launch
-
Check
logcat: look for stack traces, missing resources, class not found -
Ensure all dependencies and resource names are correct
-
Verify proper signing (certificate)
Q: Signature mismatch / “certificate does not match”
-
Some APKs validate their own signature; you may need to disable or patch it
-
Use smali to comment out or bypass signature‑checking code
Q: Custom sounds not playing
-
Confirm file path & naming
-
Check file formats (compatible codec)
-
Verify read permissions
Q: Device not recognized by ADB
-
Enable USB debugging
-
Use correct cable / drivers
-
Use
adb kill-server/adb start-server
Q: App updates break mod
-
Maintain version mapping
-
Keep mod patch scripts ready to reapply
-
Consider automating mod tasks
Conclusion & Recommendations
Modifying Zello clients can be an intriguing technical exercise—allowing UI tweaks, sound customizations, or hardware tie-ins. However, it’s fraught with legal, security, and stability risks. For serious use, adopting Zello’s SDK, Channel API, or Bridge integrations is a much safer and scalable choice.
If you decide to mod, follow rigorous practices: always backup, test on separate devices, keep your modifications minimal, and be ready to revert. And if your project scales, plan migration to the official integration paths to maintain compliance and reliability.

